

Q1. a). Identify the data types of the values given below: [1]
(i) [21,15,32] (ii) 4j
b) What will be the output of following code [1]
6 < 6 or 12
6
a) (i) List
(ii) Complex number
b) 12
True
True
False
c) A variable pointing to a value of a certain type, can be made to point to a value/object of different type. This is called Dynamic Typing.
d) An interpreter converts an High level language program into machine language line by line and simultaneously executes the converted line. A compiler converts an HLL program in machine language in one go. If there are errors in the program, it gives the error list along with the line numbers.
e) i. 1
ii. 3
f) The above statement is trying to print the value of an undefined variable name. The solution to above problem is to define the variable name before using it.
Address= Parklane, Delhi
Print(“The address is”,Address)
g) num=int(input(“Enter an integer(>500):”))
tnum=num
reverse=0
while tnum:
digit=tnum%10
tnum=tnum/10
reverse=reverse*10+digit
print(“Reverse of”, num, “is”, reverse)
Q2 a) Write the syntax to create the following list:[8,5,2,-1,-4,-7] using range function. [1]
b) Give the output of the following statement. [1]
str="Group Discussion"
print str.lstrip("Gro")
c) In which situation, would you prefer bubble sort over insertion sort? [2]
d) What happens, if we try to access a key, which is not contained in the dictionary? [2]
e) Why is Boolean considered a subtype of integers? [2]
f) Write a function calcPowers(y) that returns a tuple containing y,y2,y3 and y4. Read five integers from the user, and for each integer read, print that value raised to the powers 2,3 and 4. [3]
g) Predict the output of following code: [3]
1. x='I am the best'
print(x[:2],x[:-2],x[-2:])
print(x[:],x[:-9])
print(x[2:-3],x[-2:-5])
2. a="I" + "am" + "best"
for str in a:
b=str
print(b,':',end=' ')
3. a = 'python'
print (a[3:],a[:3])
print(a[-3:],a[:-3])
print(a[:-5]+a[-5:])
h) Consider the string str=”Global Warming”;
write statements in python to implement the following: [4]
1. To display the last four characters.
2. To display the substring starting from index 4 and ending at index 8.
3. To check whether string has alphanumeric characters or not.
4. To trim the last four characters from the string.
a) range(8, -8,-3)
b) The output will be : up Discussion.
c) Bubble sort would be ideal sorting technique in situations where data can be read sequentially(e.g., data stored in magnetic tapes)
d) The interpreter raises the Key Error exception, when a dictionary is accessed with either an undefined key or by a numeric index.
e) Boolean values True or False map to integers 1 and 0 respectively. When 0 and 1 are converted to Boolean through bool() function, they return True and False. That is why Booleans are treated as subtype of integers.
f) for n in range(%) :
y=int(input(“Enter Number:”))
P=(y, y**2, y**3, y**4
Print(number, “raised to powers 1,2,3,4 :=”, T)
g)
1. I am the be st
I am the best I am
am the b
2. I : a : m : b : e : s : t :
3. hon pyt
hon pyt
python
h)
1. print (str[-4:])
ming
2. print (str[4:8])
al W
3. str.isalpha()
False
4. print (str[:10])
Global War
Q3 a) Find the One’s compliment of –13. [1]
b) Perform the following conversions: [2]
1. EB4A16 =( )10
2. (10101110.010111)2 = ( )16
c) Simplify Y = AB’ + (A’ + B)C. [2]
d) Answer the following questions: [3]
1. A product term containing all K variables of the function in either complemented or uncomplemented form is called a __________.
2. The canonical sum of product form of the function y(A,B) = A + B is __________.
3. Product-of-Sums expressions can be implemented using ___________.
e) Simplify the given Boolean expression : [3]
AB+(AC)’+AB’C(AB+C’)
f) Draw the diagram of a digital circuit for the function F(X,Y,Z) = X’Y + Y’.Z using NOR Gate only. [4]
a) 11110010.
b) 1. EB4A16 =14x163 +11x162+4x161+10x160.
=6023410.
2. 5E.AC.
c) Y = AB’ + (A’ + B)C = AB’ + (AB’)’C = (AB’ + C)( AB’ + AB’) = (AB’ + C).1 = (AB’ + C).
d)
1. Minterm
2. A + B = A.1 + B.1 = A(B + B’) + B(A + A’) =
AB + AB’ + BA +BA’ = AB + AB’ + A’B = AB + AB’ + A’B.
3. 2-level OR-AND and NOR logic circuits
e) AB+(AC)’+AB’C(AB+C)
=AB+(AC)’+AB’CAB+ AB’CC (Distributive Law)
=AB+(AC)’+0+AB’CC (X.X’=0)
=AB+(AC)’+AB’C
=AB+A’+C’+AB’C (De-Morgan’s law)
=A’+B+C’+AB’C (X+X’Y=X+Y)
=A’+C’+B+AB’C
=A’+C’+B+AC (X+X’Y=X+Y)
=A’+C’+AC+B
=A’+C’+A+B (X’+XY=X’+Y)
=A’+A+C’+B
=1+C’+B (X+X’=1)
=1 (1+X=1)
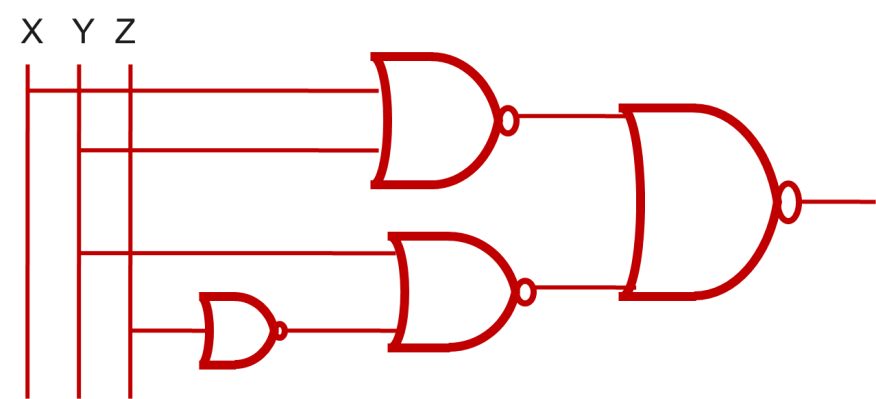
f) Logic Gate for the function
F(X,Y,Z) = X’Y + Y’. Z by using NOR gate only.
Q4 a). What is a database system? [1]
b) Write the syntax to create a table in MYSQL? [1]
c) What is a primary key? [1]
d) What is the full form of CSV? [1]
e) Mention the constraints that can be applied on the table column. [2]
f) Write down the difference between DDL and DML commands. [3]
g) Given below is the table answer the question based on it. [3]
Employee
| Emp_ID | E_Name | E_Address | E_Dept |
| 1 | ANU | CIVIL LINES BATHINDA | COMPUTER |
| 2 | BHAWANA | MALL ROAD SHIMLA | PHYSICS |
| 3 | CARROL | MG ROAD GURGAON | CHEMISTRY |
| 4 | DIA | CROSSING RPUBLIK GHAZIABAD | BIOLOGY |
1. Write the query to insert in table the 5th emp_id with its details.
2. Write the query to display EMP_ID and E_Name of an employee.
3. Write the query to change the address of Emp_ID =2 from Shimla to GUJRAT.
h) What is a data type? Explain three commonly used data type in SQL. [3]
a) A database is a collection of interrelated data and a database system is basically a computer based recordkeeping system.
b) The syntax of CREATE TABLE is:
Create table
([()],
[()…..])
c) The set of one or more attribute which uniquely identify the tuple within the relation is known as primary key.
d) CSV stands for “comma-separated values”.
e) NOT NULL, DEFAULT, UNIQUE, CHECK, Primary key, Foreign Key are some of the constraints that are applied to table column.
f) DDL: data definition language is used to define the data structure. The statements included in DDL are: create, alter, drop, truncate, comment and rename.
DML : Data manipulation language is used to manage data within schema object. The statements included in it are: select, insert, update, delete and merge.
g)
i) INSERT INTO Employee
VALUES ( 5, ‘TIA’, ‘Model Town’ , ‘MATHS’)
ii) select EMP_ID and E_Name from Employee
iii) UPDATE Employee SET E_Address=MALL ROAD GUJRAT where Emp_ID=2
h) SQL Data type defines the value type that can be stored in a table column. For example if we want to store the number in a table we can store it as int data type.
The commonly used data types are:
Q5 a) What do you mean by Plagiarism? [1]
b) Describe why authentication is important for file protection. [2]
c) Mention any two preventive measures against viruses. [2]
d) What is Digital footprint? Why is it so important? [2]
e) Enlist three measures one should take to avoid loss of confidentiality of personal information. [3]
a) Plagiarism is stealing someone else’s work and representing it as our own work without giving credit to creator.
b) Authentication ensures that the individual is who he or she claims to be, but says nothing about the access right of the individual. It is used as a primary step for file protection from unauthorized users.
c) The preventive measures are:
d) A digital footprint is the information of data that we create while browsing internet.
It is important as it keeps the record and traces of activities that people do on internet so that this information can be tracked.
e) The three measures are:-

Take your CBSE board preparation to another level with AI based and rich media animation on Extramarks - The Learning App.
Features of Learning App