Informatics Practices 2015 CBSE [Delhi] Set IV
To Access the full content, Please Purchase
-
Q1
(a)A school with 20 stand-alone computers is considering networking them together and adding a server. State 2 advantages of doing this.
(b) Distinguish between LAN and WAN.
(c) What is the purpose of Modem in network?
(d) Write one example of IP address.
(e) Define ‘Domain Name Resolution’.
(f) Name two threats to security in a network. What is the role of Firewall in Network security?
(g) Write one advantage and one disadvantage of Open Source Software over Proprietary software.
Marks:10View AnswerAnswer:
(a)Advantages to form the computer network is:
- Sharing of resources
- Centralised database
- Sharing of data
- Low cost
(b)LAN is confined to one or a nearby building. However, Internet has no geographical area and is the collection of different LANs. WAN spans a larger geographical area, often a country or continent. Internet is an example of WAN.
(c)A modem is a computer peripheral that allows connection and communication with other computers via telephone lines. Modem converts digital signals to (A/F) Audio Frequency tones which are in the frequency range that the telephone lines can transmit and also it can convert transmitted tones back to digital information.
(d) An IP address has four numbers separated by dots, where each number has a value of 1 to 255.
For example: 198.230.2.3
(e)Domain Name Resolution is the task of converting domain names to their corresponding IP address. When a domain name is entered to use an application over the Internet, the application will issue a command to have the operating system convert the domain name into its IP address. This IP address is used to connect that application to the computer over the server so that the desired operation can be performed. The way the operating system resolves the domain name is based upon its configuration.
(f) Two threats to security in a network are-
1. Denial of Service (DoS) Attack-Denial of Service is considered as an attack where a malicious user intentionally disrupts the service to a computer or network resource.
2. Intrusion Problems/Access Attacks- Intrusion problem occurs when an unauthorised user attempts to gain access to confidential and sensitive information.A firewall is a security system that acts as a protective boundary between a network and the outside world.We can use firewalls to protect an access from external network communicationvia telephone or internet. Firewall can be software based or hardware based.
(g) Advantage of Open Source software over Proprietary software-
An Open Source software can be freely distributed and used where as Proprietary softwares neither open nor freely available.
Disadvantage of Open Source software over Proprietary software-
Open source softwares are difficult to understand i.e., it may require training whereas, Proprietary softwares are easy to understand and more secure than the Open Source software.
-
Q2
(a) Write the value of variable ‘c’ after execution of the following code:
int d;
int c;
d=7;
c=(5*++d)%3;
(b) What is the difference between jTextField and jPasswordField components?
(c) In a SWITCH statement, what is the purpose of ‘default’ section?
(d) After typing the HTML code using a text editor, how do you see how it would look as a web page?
(e) Write Java code to assign the value 500 to variable x. Increase the value of x by 50 and store it in variable y.
(f) Write the output that will be generated by the code given below
int i;
i=7;
int r;
r=8;
while(i<=10)
{
System.out.println(r*i);
i=i+2;
}
(g) “With XML there are no predefined tags”- Explain in brief with the help of an example
Marks:10View AnswerAnswer:
(a)The value of variable ‘c’ after execution of the code will be 1.
(b)The jTextField accepts the input given by the user in human readable form whereas, the jPasswordField control accepts the input given by the user in human non-readable form. Asterisk (*) is the default symbol that is displayed to the user in place of entered text.
(c)Switch statement is a multiple branch selection statement. It allows you to test the value of an expression against the list of integer or character.If the match is found the statement associated with the match are executed. If no match is found then the statement written under ‘default’ section will execute.
(d) After typing the HTML code using a text editor follow the steps mentioned below to view it as a web page.
- Open the Browser window
- Now in the address bar, type the HTML document’s name along with its path and press Enter .
OR
- Open the Browser window
- Go to File menu and click on option Open File.
- Now in the, open dialog firstly choose the place from the pane and select the desired .htm or .html file
(e) Code-
int x,y;
x=500;
y=x+50;
System.out.println(“x=” +x);
System.out.println(“y=”+y);
(f) Output of the given code will be-
56
72
(g) XML is eXtensible Markup Language which allows to create application specific structured documents by allowing creation of new tags. These structured documents can later be rendered in different way.
XML allows creation of new tags or markup languages therefore, it does not contain any predefined tags.
-
Q3
(a) What is MySQL?
(b) Is NULL, value the same as 0(zero)? Write the reason for your answer.
(c) Write the UPDATE command to increase the commission(Column name: COMM) by 500 of all the Salesmen who have achieved Sales( Column name: SALES) more than 200000. The table’s name is COMPANY.
(d) While using SQL pattern matching, what is the difference between ‘_’ ( underscore) and ‘%’ wildcard symbols?
(e) How is primary key constraint different from Unique key constraint?
(f) Write one similarity and one difference between CHAR and VARCHAR data types.
(g) What is a Transaction? Which command is used to make changes done by a Transaction permanent on a database?
Marks:10View AnswerAnswer:
(a)MySQL is an open source relational database management system. It is used to manage the data electronically. The data in MySQL is stored in the form of rows and columns called tables. Such database application softwares are very helpful in maintaining the information with the help of an application.
(b)The NULL value is not same as 0. The 0 is the value for an integer variable that indicate no value, whereas using NULL actually indicates that there is nothing, so there is no value.
Using NULL is preferable, because if you decide to add some referential integrity constraints in the future, then NULL values will work.
(c) UPDATE COMPANY
SET COMM=COMM+500
WHERE SALES>200000 AND Job="Salesman";
(d)The ‘_‘allows to match any single character whereas ‘%’ allows to match an arbitrary number of characters including zero values as characters.
(e)A PRIMARY KEY constraint is used to uniquely identify the fields. The UNIQUE KEY is similar to PRIMARY KEY with the following differences-
- A table can have at most one PRIMARY KEY constraint but it can have as many as you want UNIQUE KEY constraints.
- Columns that are part of the PRIMARY KEY must be defined as NOT NULL. That is not required for columns that are part of UNIQUE KEY constraints.
(f) Similarity- Both char and varchar data types are used to define string values.
Difference- The char data type specifies the fixed length that is declared during the table creation. Whereas, the values in VARCHAR columns are variable-length strings.
(g)A transaction is a logical unit of work (LUW) that must succeed or fail in its entirety. A transaction is an atomic operation which may not be divided into smaller operations.
The COMMIT command is used to make changes done by a Transaction permanent on a database.
-
Q4
The following code has some error(s). Rewrite the correct code underlining all the corrections made
a) int marks, temparatures;
temperatures = Integer.parseInt(jTextField2.getText());
if(marks<80) and (temperature >=40)
System.out.println(“Not Good”);
}
(b) How many times will the following WHILE loop execute?
int y=7, sum=0;
while(y<=15)
{
sum=sum+y;
y=y+2;
}
(c) Rewrite the following program code using IF ELSE IF instead of SWITCH statement:
String tour;
int cl = Integer.parseInt(jTextField1.getText());
switch(cl)
{
case 8: tour= “n You are going to Camp Ramgarh”;
break;
case 9: tour=”n You are going to Manali, Rohtang Pass”;
break;
case 10: tour=”n You are going to Chail”;
default : tour=”No school tour for you this time”;
}
(d) Write the value of sum and x after execution of the following code:
int sum,x;
sum=7;
x=5;
sum=sum+(x++);
(e) What will be the contents of jTextField1 and jTextField2 after executing the following code:
String a = “Baat”;
jTextField1.setText(s.length()+ “ “);
jTextField2.setText(a.toUpperCase());
(f) The students of “Shiksha Vidyalaya“ work for different extra curricular ativities like ‘Community Outreach Programme’, ‘Swachh Bharat Abhiyan’ and ‘Traffic Safety Club’. The Programmer at the school has developed a GUI application as shown below:
- A student can participate in more than one activities.
- Each student gets 10 points for each activity- namely Community Outreach Program, Swachh Bharat Abhiyan and Traffic Safety Club.
Help the programmer to write code for the following:
- When ‘Calculate Total Score’ button is clicked, the points for each activity( that is selected) should be displayed in the text field in front of that activity’s checkbox and the Total Score should be displayed in the appropriate Text field.
- When Clear button is clicked, all the Textfields and Checkboxes should be cleared.
- When Stop button is clicked, the application should close.
Marks:15View AnswerAnswer:
(a)Corrected code-
int marks, temparatures;
temperatures = Integer.parseInt(jTextField2.getText();
if((marks<80) && (temperature >=40))
{
System.out.println(“Not Good”);
}
else
{
System.out.println("OK");
}
(b)The while loop will execute 5 times.
(c)
String tour;
int cl = Integer.parseInt(jTextField1.getText());
if(cl==8)
tour= “n You are going to Camp Ramgarh”;
else if(cl==9)
tour=”n You are going to Manali, Rohtang Pass”;
else if(cl==10)
tour=”n You are going to Chail”;
else
tour=”No school tour for you this time”;
(d)The output will be:
sum=12
x=6
(e)After executing the code the control jTextField will contain value 4 whereas jTextField2 will contain value ‘BEST’.
(f)
(i)
private void btncalculateActionPerformed(java.awt.event.ActionEvent evt) {
int total=0;
if (chk1.isSelected())
{
total=total+10;
txtoutreach.setText(""+ 10);
}
if(chk2.isSelected())
{
total=total+10;
txtswachh.setText(""+10);
}
if(chk3.isSelected())
{
total=total+10;
txttraffic.setText(""+10);
}
txttotal.setText(""+total);
}
(ii)
private void btnclearActionPerformed(java.awt.event.ActionEvent evt) {
txtrno.setText("");
txtname.setText("");
txtoutreach.setText("");
txtswachh.setText("");
txttraffic.setText("");
txttotal.setText("");
}
(iii)
private void btnstopActionPerformed(java.awt.event.ActionEvent evt) {
System.exit(0);
}
-
Q5
(a) Distinguish between Single Row and Aggregate functions of MySQL. Write one example of each.
(b) Consider the following table named “SOFTDRINK”. Write commands of SQL for (i) to (iv) and output for (v) to (vii).
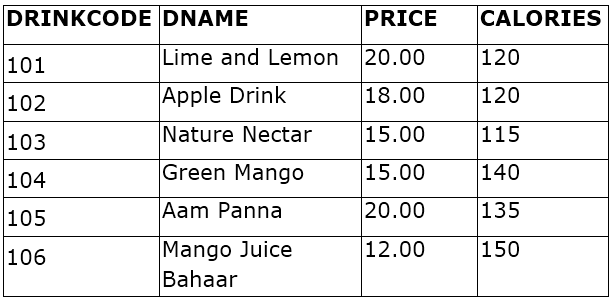
(i) To display names and drink codes of those drinks that have more than 120 calories.
(ii) To display drink codes, names and calories of all drinks, in descending order of calories.
(iii) To display names and price of drinks that have price in the range 12 to 18(both 12 and 18 included).
(iv) Increase the price of all drinks in the given table by 10%.
(v) SELECT COUNT( DISTINCT(PRICE)) FROM SOFTDRINK;
(vi) SELECT MAX ( CALORIES) FROM SOFTDRINK;
(vii) SELECT DNAME FROM SOFTDRINK WHERE DNAME LIKE “Mango”;
(c) What is the degree and cardinality of ‘SOFTDRINK TABLE’?
Marks:10View AnswerAnswer:
(a)Single row functions are the one who work on single row and return one output per row. For example, length and case conversion functions are single row functions.
Example- DELETE table;
The aggregate functions are also called multiple row functions that works upon group of rows and return one result for the complete set of rows. They are also known as Group Functions.
Example: COUNT(), SUM()
(b)
(i)SELECT DNAME,DRINKCODE
FROM SOFTDRINK
WHERE CALORIES>120;
(ii)SELECT DRINKCODE, DNAME, CALORIES
FROM SOFTDRINK
ORDER BY CALORIES DESC;
(iii)SELECT DNAME, PRICE
FROM SOFTWARE
WHERE PRICE BETWEEN 12 AND 18;
(iv)UPDATE SOFTDRINK
SET PRICE=PRICE+(PRICE*.10)
(v) OUTPUT-
4
(vi) OUTPUT-
150
(vii) OUTPUT-
Green Mango
Mango Juice Bahaar
(c)Degree-4
Cardinality- 6
-
Q6
(a) Write MySQL command to create the Table ‘LIBRARY’ with given constraints.
Table : LIBRARY
COLUMN_NAME
DATETYPE(SIZE)
CONSTRAINT
BookId
Int(10)
Primary Key
BookName
Varchar(40
Not Null
Type
Char(4)
Author
Varchar(40)
No_Copies
Int(6)
Price
Decimal(8,2)
(b) In a Database Company, there are two tables given below:
Table: SALES
SALESMANID
NAME
SALES
LOCATIONID
S1
ANITA SINGH ARORA
250000
102
S2
Y.P. SINGH
1300000
101
S3
TINA JAISWAL
1400000
103
S4
GURDEEP SINGH
1250000
102
S5
SEMI FAIZAL
1450000
103
Table: LOCATION
LOCATIONID
LOCATIONNAME
101
Delhi
102
Mumbai
103
Kolkata
104
Chennai
Write SQL queries for the following
(i)To display SalesmanID, name of salesmen, LocationID with corresponding location names.
(ii)To display names of salesmen, sales and corresponding location names who have achieved sales more than 1300000.
(iii)To display names of those salesmen who have ‘SINGH’ in their names.
(iv)Identify Primary key in the table SALES. Give reason for your choice.
(v)Write SQL command to change the LocationID to 104 of the Salesman with ID as S3 in the table ‘SALES’
Marks:10View AnswerAnswer:
(a)
Create Table LIBRARY
(BookId Int(10) primary key,
BookName Varchar(40) Not Null,
Type Char(4)
Author Varchar(40),
No_Copies Int(6),
Price Decimal(8,2));
(b)
(i) SELECT S.SALSESMANID, S.NAME, S.LOCATIONID, L.LOCATIONNAME
FROM SALES S, LOCATION L
WHERE S.LOCATIONID=L.LOCATIONID;
(ii) SELECT S.NAME, S.SALES, L.LOCATIONNAME
FROM SALES S, LOCATION L
WHERE S.LOCATIONID=L.LOCATIONID AND
S.SALES> 1300000
(iii) SELECT NAME FROM SALES
WHERE NAME LIKE”%SINGH%”;
(iv)The field SALESMANID will be the primary key of the table because it is containing unique values for each row of the table.
(v) UPDATE SALES
SET LOCATIONID=104
WHERE SALESMANID=S3;
-
Q7
(a) How does e-learning allow students to study at their own pace?
(b) How does e-governance empower citizens? Write one point.
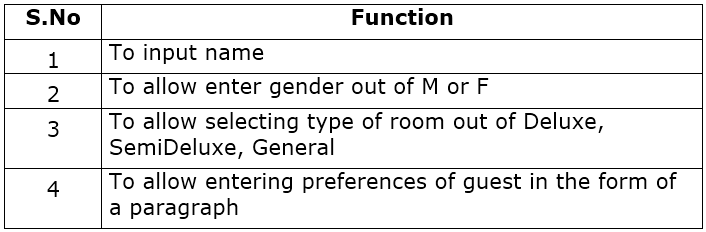
(c) Sabeena is creating a form for the hotel where she works. Help her to choose most appropriate controls from ListBox, ComboBox, TextField, TextArea, RadioButton, Checkbox, Label, and Command Button for the following entries:
 Marks:5View Answer
Marks:5View AnswerAnswer:
(a)Benefits of e-Learning to the Learner/student include:
- On-demand availability enables students to complete training conveniently at off-hours or from home.
- Self-pacing for slow or quick learners reduces stress and increases satisfaction.
- Self-Motivated interactivity engages users, pushing them rather than pulling them through training.
- Successfully completing online courses builds self-knowledge and self-confidence.
(b)e-Governance is the process of using IT for automation of both internal activities or operations of the government and its external interactions with citizens and other governmental agencies. e-Governance involves applications which are used by government agencies or organisations to provide better government.
(c)